A report by WSJ tells the story of a data breach on Capital One’s server hosted on AWS (a cloud platform). The hacker broke through the bank’s firewall and stole the financial data of more than 100 million customers. The company remained unaware of this breach until months later when a good Samaritan pointed them in the direction of a GitHub repository where the hacker had deposited their data.
What ensued was a public scandal referred to as one of the biggest data breaches in the 21st Century. This is what we call an epic screwup, one that Capital One had to pay $80 million in fines and penalties for. They also suffered a blow to their reputation.
The more data and sensitive assets a company handles, the more of a target they become for online attackers. But we live in a data-driven world; data is life and hackers are so resilient. Let's face it, they'd be admirable if they weren’t so nefarious.
One little mistake or oversight and your sensitive data may end up on the receiving end of a hyperlink on social media. Nobody wants that.
This article explores what an application security engineer’s roles and responsibilities are, what skilled weapons they wield, and why you need them on your team.
What is the goal of application security in a business?
Businesses are increasingly software-based and data-driven, so much so that almost every business uses some form of software and relies on data to make intelligent decisions. From simple web apps to advanced business tools, every company is slowly becoming a software and data company.According to a study by PurpleSec, there were over 30,000 cyberattacks per day (over 30 million per year) in 2018. Their statistics also reveal that cybercrime has been up 600 percent due to the pandemic and that by 2021, a new organization will fall victim to ransomware every 11 seconds.
The main goal of application security is to protect your business applications from security attacks by developing, inserting, and testing security components that make your application more secure.
As straightforward as this may seem, attacks come in various forms. Technology infrastructure includes various layers (network, endpoint, data, server, and application) and while security across all layers is important, Forrester’s 2020 State of Application Security Report revealed that the application layer is the most vulnerable to external attacks. They also cited open-source software as the chief concern for application security.
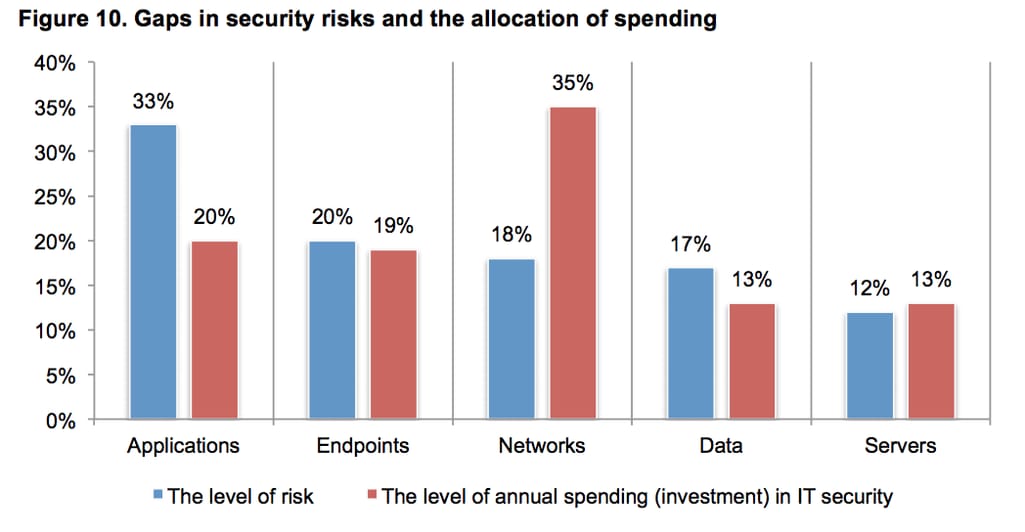
Ponemon Institute’s Research Report agrees with Forrester’s. Their chart (shown above) shows that the threat of application security outweighs the efforts currently being expended to curb it. Understanding why application security is important centers on being aware of some of the vulnerabilities that leave your application open to attacks.
For one, integrating open source code and APIs increases the opportunities for vulnerabilities as applications rely on traffic from these APIs and malicious files could pass through unfiltered.
Also, your application’s code is written by developers who are not beyond mistakes. These mistakes could be as evident as errors in a few lines of code or it could be that the entire code base leaves loopholes that could be exploited.
Vulnerabilities could also come from aspects that are not directly related to code at all. Weak passwords are a good example. Websites and applications that allow weak passwords are more vulnerable to bad actors than those that enforce strong ones. That’s why many sites have standards for the types of passwords users are allowed to create.
So why do you need application security for your business?
To prevent potential attacks. Application security involves proactive steps to discover vulnerabilities and patch them before hackers get a chance to exploit them. This could involve constant and dynamic app security testing and is one of the application security engineer’s roles and responsibilities.
To secure sensitive information. In addition to preventing potential attacks, businesses need to guarantee that even genuine users cannot access data that they’re not allowed to.
To make customers trust you more. It takes one data leak to bring down the reputation a business has worked hard to build. The resulting loss of confidence from a data breach can tank even great companies.
Protecting your business’s data is just as important as making profits, and it is only those with application security engineering skills -- not your developers -- that are sufficiently qualified to protect your applications.
To understand what an application security engineer’s roles and responsibilities are, you first need to understand what they do daily.
What does an application engineer do?
A great way to explain what an AppSec engineer does is to explain what they don’t do. Application engineers are not developers. Although they know the full software development life cycle, the application security engineering skill set does not include developing business applications.However, much of their job is done during the business application’s development stage. They work with developers to set up security control measures during every stage of software development. They also use tools and techniques to protect applications that have been deployed. On a rolling basis, an AppSec engineer will implement the different types of application security.
Authentication. Implementing systems that ensure that users are who they say they are. The most basic form is a username and password, but more advanced forms of authentication have been developed.
Authorization. This layer ensures that the user has permission to use the application or the components they are trying to access. If they are, they can. If not, their access is blocked.
Encryption. This prevents attackers as well as genuine users from accessing information they are not authorized to see, especially with data in transit.
Logging. AppSec engineers set up monitoring to help identify culprits in case of a data breach and to keep track of the application’s behavior.
Application security testing. This include specific tests that AppSecs run to reveal application vulnerabilities (more on this later).
Application security engineering roles and responsibilities
Application security engineering roles and responsibilities span the entire software development life cycle. And while the industry may be fast paced and their duties may evolve, the following describes the core of what they do.Setting development parameters
AppSec engineers set security controls and design requirements during the software creation and development stage of the software lifecycle. They also integrate these designs into the software.The application security engineer ensures that security across all aspects of the software is uniform by setting up checkpoints.
Testing source code and running code
Static AppSec testing (SAST). The AppSec engineer analyzes your application’s source code for vulnerabilities before compiling and running them. This goes hand in hand with security measures in the development stage to avoid security loopholesDynamic AppSec testing (DAST). Security depends on software responding to inputs in a predetermined way. Dynamic testing analyzes running code by running attack simulations and studying how the application responds. These simulations often employ the same techniques hackers use to break into applications and they reveal vulnerabilities that the engineer can patch so the app remains secure in case of a real attack.
Interactive testing. Combining the best parts of both static and dynamic testing, interactive testing analyzes code when its functionality is being engaged. In other words, it is analyzing code when a user is interacting with the application.
Mobile testing. Here, mobile apps are tested for their app functionality (UI/UX, business flows), real environment conditions (gestures, network), performance, accessibility, and availability.
Email testing. Email testing is an essential part of any marketing, transactional email campaigns. AppSec engineers make sure that technical parameters of emails look right, have correct HTML, get the highest deliverability, and each email protocol works properly.
Implementing advanced security features
The AppSec engineer, after testing applications, implements patches and utilizes shielding tools that harden applications, making them less vulnerable to attacks. Some of these processes include:Runtime application self-protection. A combination of testing and shielding that protects applications from reverse engineering attacks. These tools also monitor the application’s behavior and can stop certain code/functions from running and even terminate the application if the need be.
Code obfuscation. This involves hiding your source code from hackers so it can’t be attacked. Other methods involve encryption and using threat detection tools.
Managing user authorization
Cryptography is a strong part of an application security engineer’s skills as they will continuously manage who has access to certain resources. Your application security engineer will encrypt data in your application and its supporting databases as well as file storage systems to avoid attacks from hackers or even genuine users without authorization.Cryptography is especially important when components of your application run in the cloud or share sensitive information with cloud-based APIs or VMs. For example, if you use cloud infrastructure to run big data operations, you’d want to encrypt your data before uploading it to the cloud.
Threat modeling
Threat modeling is a process AppSec engineers use to determine the most dangerous or potent threats to an application and where their applications are most vulnerable. This process helps direct the application security engineer’s skills to where it can be most utilized.The engineer breaks the application into components, documenting them, and outlining the flow of data between the components. They then explore the threats that each component is exposed to and ranks them on a severity scale after which they document the countermeasures already in place as well explore new countermeasures that could be developed.
Alternatively, your engineer could list all entry points and then write down all assets that an attacker may want to obtain, along with their business impact. They rank these entry points based on value and develop countermeasures accordingly.
Maintaining technical documentation
While documentation is not a widely known AppSec engineering responsibility, it's one that is important, especially in large organizations with several applications and in cases where AppSec engineers work with development teams.What skills should you look for when employing an AppSec Engineer?
Unlike many other technical roles, there are no entry-level application security engineers and business leaders must ensure that their application security engineer’s skills are backed by academic qualifications and experience.Certifications
It’s common practice in the technology space to forego candidates with computer science degrees for developers with hands-on experience. Well, with AppSec engineers, you’ll need both.Application Security certifications go a long way to show that candidates possess certain knowledge that is crucial to their role. Some certificates to be aware of are below.
Certified Systems Security Professional (CISSP). Given by the International Information System Security Certification Consortium, also known as (ISC), this certification has been granted the same standing as a master’s degree in the UK by the UK National Recognition Information Centre.
Certified Information Security Manager (CISM). An advanced certification indicating that its holder possesses the knowledge and experience required to develop and manage application security at an enterprise level.
Certified Information Systems Auditor (CISA). While not as renowned as the CISM, this certification guarantees an engineer’s ability to monitor, audit, and control IT and business systems. However, this is an entry-level certification and must be backed by more advanced ones.
Certified Hacking Forensics Investigator (CHFI). Focuses on investigating attacks as well as extracting evidence to report a cybercrime (useful in cases of financial breach) and prevent future attacks.
Practical skills
This is where good AppSec engineers shine. Here’s what any engineer worth his salt should have.Thorough understanding of attacks and threats. Cyberattacks can come anytime and in any form. Your engineer should know the common threats and attacks and the techniques hackers usually use to perpetrate them. They should also know how to manage vulnerabilities.
Ethical hacking. Ethical hackers test an application for vulnerabilities by hacking it themselves, working at the request of the company, of course. While it may not be compulsory for your engineer to be an ethical hacker, he must be familiar with the practice and must be able to collaborate with one.
Cryptography. Your AppSec engineer must be able to secure data both at rest and in transit. Database encryption, cloud encryption (for cloud-based applications) should be a highlighted skill.
Experience with malware. Some hackers use code obfuscation to hide their malware code. Your AppSec should be able to protect against such intrusions. They should have experience defending systems against malware. Of course, with intrusion protection comes experience with firewalls which you should be in your application security engineer’s skill set.
Threat analysis and modeling. Your AppSec engineer should take a proactive approach to dealing with threats by using threat analysis to determine the most vulnerable components of your application and fortifying them.
Technical writing. While it may be argued that documentation is not a hard skill, your AppSec engineer will need to keep detailed documentation of the tools and techniques being used, the most valuable components of the application, and even common threats to the application.
Soft skills
Application security engineers will work with developers and other technical teams. Consequently, they should have good communication skills and a cooperative spirit. They should also be flexible enough to adapt to changing application requirements and evolving technologies.As people who adopt proactive security measures, they should be creative so that they can conjure up less obvious ways that your system may be at risk. They should also be able to perform under pressure in cases of severe breaches.
Lastly, your application security engineer should be a continuous learner, especially when working in an agile environment.
Why you should consider hiring a remote AppSec Engineer
If all the wonderful things that hackers can do to your application once they get a hold of it isn’t a good enough reason to hire a remote AppSec engineer, then consider some of these.Cyberattacks are usually time critical. You must act quickly and stop the risk of losing your data. If your development team missed a security step or inadvertently left their code open to attacks, having an AppSec engineer on retainer is invaluable at those times.
Secondly, for agile environments that involve continuous deployment and integration, there are no set release schedules. You’ll need a remote engineer available in different time zones to secure every iteration of your software.
For custom business applications, you’ll need an AppSec who knows its components inside out, especially when carrying out threat modeling. Hiring an AppSec engineer only when you have security issues may put you at a disadvantage as they may need to first get their head around your application.
Also, you may not want to release source codes and other highly sensitive documents to a freelancer, so hiring a full-time, in-house remote engineer is the best bet for your business.
For companies handling sensitive digital assets like customer financial information, there are data protection standards your system must adhere to, like the GDPR and HIPAA, data protection standards as well as the 23 NYCRR 500 Cybersecurity regulation for financial data. Security engineers ensure you don’t violate these standards.
Finally, a remote AppSec engineer doesn’t have to come into the office. You can hire the best talent that may be on the other side of the world and collaborate like you were in the same room.
With businesses becoming more data-oriented and cybercrime on the rise, you may find that an application security engineer’s skill may be your best defense against breaches, leaks, and other attacks by villainous hackers.
 Gabriela Molina is the writer and editor of the DistantJob blog. As a former freelancer, she has covered a wide range of topics throughout her career. She is currently specializing in the areas of technology, leadership, and remote work.
Gabriela Molina is the writer and editor of the DistantJob blog. As a former freelancer, she has covered a wide range of topics throughout her career. She is currently specializing in the areas of technology, leadership, and remote work.Want to write an article for our blog? Read our requirements and guidelines to become a contributor.
