Are you the type that starts a workday long before stepping into the office and firing up your computer? Most of us get business emails on our phones and start messaging coworkers as we commute. Back in 2012, Forrester found that 67 percent of employees with smartphones chose them personally without any corporate guidance. And a year later, a McAfee survey suggested that 80 percent of employees regularly use unapproved SaaS apps at work.
So, BYOD (bring your own device) is no longer a trend. It’s reality. The boundary between workstation and mobile is so fuzzy, the question isn’t if we embrace enterprise mobility, but rather how we do it.
For instance, The Walsh Group, a construction firm, embraced the BYOD demand to let their project managers share critical project information straight from the construction sites instead of going back to an office and configuring blueprints from there. This increased their cost estimation speed by 20 percent and put the company ahead of competition. For one of our clients, AltexSoft developed a customizable app for production workers to complete digital checklists when on-site, track machinery performance, take photos of malfunctioning hardware, etc. This allowed for rapid reaction and on-time employee tracking.
On the other hand, if you handle those devices or let employees use their own, you should acknowledge that humans are the weakest link in any data security structure. People lose smartphones, they install harmful software, copy information and irresponsibly paste it, or just let others access it.
That’s the problem worth considering.
How do you control access to sensitive corporate data? How do you ensure that employees won’t irresponsibly share this data? And, more importantly, how do you manage the use of mobile devices without invading employee privacy?
The second scenario entails employees accessing corporate data when using devices for professional purposes and a company paying their cell phone bills.
Another scenario depicts employees using their devices for work and leisure, with a company choosing cell phone service options and paying for them.
Advantages: The BYOD model is convenient for users and beneficial for employers who don’t have the expense of purchasing devices.
Disadvantages: This model comes with security and management concerns due to the uncontrolled use of various devices. For example, an IT department can’t develop a unified support system due to a variety of device types and models used in an office. Employers must also consider how they will retrieve data from a worker’s device if he or she leaves the company. When the former team member worked in the sales department, special attention to data retrieval is required.
Ideally, employees must take responsibility for the integrity of business information when using a personal smartphone or tablet to reply to corporate emails, fill out checklists, or open and edit documents. The reality is that a company has to establish device use policies, explain them to employees, and implement technical solutions to help them keep both devices and data safe. So, the second and third BYOD scenarios require company solutions to technical and legal issues.
Advantages: With the COPE approach, IT departments don’t struggle with device control and protection as they know exactly how many and which devices workers have on hand. Another advantage of COPE is that organizations are free to install management software and/or integrate devices in mobile device management systems. And, we’ll talk more about that below.
This model allows for solving regulatory and legal issues connected with wiping off data on lost or stolen devices. As device owners, organizations can avoid a situation in which they have no right to remotely delete corporate data on personal devices (companies are restricted from doing so in some European countries.)
Disadvantages: The need to purchase devices is one of this model's disadvantages. Companies nevertheless can cut costs if buying devices in bulk. Employers also have more opportunity to negotiate for better service contracts because of the number of potential customers they can deliver. And as employees are responsible for keeping devices in a good technical state, the IT department can save time and money. They usually contact a device vendor or a company’s technical support only if a problem is complex.
A worker is free to use a device they chose both for work and personal purposes. An organization maintains it by installing necessary apps and updating when needed. Usually, employees aren’t granted administrative privileges. That’s why workers must notify the IT staff about any significant settings they want to make.
Advantages: CYOD simplifies the work for the IT team because it monitors and supports a limited number of device types and models. CYOD is a good choice for companies working with sensitive information. A company has the full control over devices and can install any security software it chooses. So, corporate data is protected from unauthorized access even if a device was stolen.
Disadvantages: The implementation of CYOD has its challenges. Organizations have to spend a substantial amount of money for the purchase and/or maintenance of hardware. It’s also important to regularly update a list of approved devices not to miss new applications and technologies. Companies can keep current about cutting edge technologies with application delivery.
User dissatisfaction is another risk factor. Employees may not like the performance of the devices allowed in a company, leading to lower productivity.
One more thing to consider before going CYOD is that maintenance of different device types takes more effort for the IT team. A company has to be sure it can afford such an initiative.
There are six enterprise mobility components:
Now let’s discuss them in detail.
Major functionality to consider:
Obviously, each vendor integration scenario may differ, but generally, the following steps are advised:
Application management. The MAM features are designed to meet the BYOD scenarios, when your employees actively use their own devices for work but aren’t thrilled about letting an organization intrude on their private lives. Employee use of a single device where private and work-related usage mix may raise a number of security concerns. MAM allows for decoupling personal and job use by managing applications without sacrificing users’ privacy. This means that you can impose rules and regulation for work-related apps allowing free use of the others.
Some things to consider:
Most EMM systems–like industry leader AirWatch–have geofencing support. This allows for defining geographic zones connected with specific policies. For example, many hospitals provide their staff with tablets having clinic management software to record patients’ symptoms and instantly retrieve patient-related information. To ensure that sensitive patient data is safe, geofencing can lock this tablet if it were to leave the hospital’s defined perimeter. Basically, you can tether any policy to a device’s geographic zone.
How to integrate apps with application management solutions. Like identity management, popular EMM vendors support integration with certain apps available at the AppStore or in Google Store. If your app isn’t on the list of supported ones, you’ll need programming to enable this integration. Usually, there are two paths you can take:
Virtualization can be done through hypervisors and containers.
Hypervisor (also known as virtual machine monitor/manager) is a software used to create and run multiple operating systems (OSs) on a device (host machine). The additional OS is called a virtual (guest) machine (VS).
Containers allow for abstracting applications from one computing environment to another. They provide a virtual isolated platform for applications to run on.
There are two types of virtualization via hypervisors.
Bare-metal virtualization. This type of hypervisor runs directly on the device hardware and has access to its resources. This allows for optimizing performance of both OSs. As these OSs are completely separate from each other, possible crashes, errors, or malware attacks on the former OS won’t affect the latter.
Because of such placement, bare-metal hypervisors are developed specifically for hardware visualization. In other words, they manage and control the work of numerous applications within various VMs. That’s the reason IT departments prefer to use them in production.
Hosted virtualization. This hypervisor runs within a host mobile system software environment, between the hosted OS working on the second software level and a guest OS that runs on the third software level. The hypervisor is installed on top of the guest OS, like any other app. This virtualization approach is less secure because the performance of the guest OS depends on the host OS. So, the guest operating system may fail if the host is attacked.
How to implement virtualization via hypervisors. The biggest virtualization vendors — VMware, Microsoft and Citrix Systems — provide hypervisors of both types. If bare-metal hypervisors work best for you, then consider such hypervisors as Oracle VM server, Microsoft Hyper-V, and ESX or ESXi by VMware. When looking for a hosted hypervisor, think about installing Microsoft Virtual PC, Oracle VirtualBox, Workstation, Server, or Fusion by VMware.
Containers store files, system libraries, and environment variables — the components needed to run a specific software. The host OS also restrains the container's access to physical resources like CPU and memory. Thanks to this, the container uses less of the host OS physical resources.
The mobile device has personal and enterprise environments. The work environment is supported by the IT administrators, while a user is free to do anything within the personal environment. The container can be deleted if a device is stolen, lost, upgraded, or if an employee leaves the company.
How to implement container-based virtualization. Many tools for containerization are available on the Internet, both open source and paid. Here are some of the free options you can choose from.
Docker is one of the most popular providers of containerization tools. Its open source platform allows for creating and operating containers for Linux- and Windows-based apps. Docker containers are portable: You can move them among any system that shares the host OS without changing code.
Kubernetes, another free container orchestration engine, also has a big user community. The tool can help you control and maintain the work of numerous containers, so it’s especially valuable if you have to manage large-scale operations. The Kubernetes platform can be integrated with the Docker platform.
OpenShift is a powerful container management platform that “brings Docker and Kubernetes to the enterprise.” Integration with the latter engine allows users to automate development, deployment, maintenance, and scaling of containers.
While virtualization via hypervisors or containers and virtual desktop infrastructure (VDI) allows organizations to solve similar management and security problems, they significantly differ in the data storage approach.
VDI (sometimes called server-based computing) entails running and managing a desktop OS in a data center instead of a local computer, thin client, or mobile device. The desktop image is delivered on-demand via a remote display protocol, while corporate information is securely stored in a data center. It has no difference for the user.
At the hardware level, VDI consists of a group of host machines providing computing power to connected devices.
Organizations may choose between persistent and nonpersistent approaches to VDI. The former is about providing a worker with a personal desktop image that can be configured according to their needs. The latter entails visualized desktops for public use within the organization. These desktops return to their original state after a user logs out.
Advantages: Besides ensuring safety for data, VDI allows for cost savings related to infrastructure upgrade. Thanks to a little computing taking place at endpoint devices, IT can turn obsolete desktops into VDI clients extending their lifespan. And when it’s time to buy new machines, a department can get less powerful ones.
However, the storage of OS, data, apps, and settings for users required for persistent VDI at a data center may come at a high price. So, a company must determine it has enough resources to use this visualization technology.
Disadvantages: VDI also has some drawbacks. The network connection may fail at times, and if it does, the whole team’s productivity is in danger. The licensing and support for software is another VDI’s weak spot. Companies using noncustomized desktop images have even more chance of facing problems with licensing. The reason is that some agreements prohibit providing software for numerous devices.
How to implement virtual desktop infrastructure. The first thing you should do is to compare VDI platforms in the market. We suggest looking at XenApp and XenDesktop by Citrix (the vendor provides a 90 day trial period), Horizon 7 by VMware, and solutions from Microsoft.
Yet, as always, there are some limitations. For instance, if you are a Microsoft fan and its products are ubiquitous in your organization, it’s likely that you store information in Office files. Well, it’s better to use Azure Rights Management if you do, because Microsoft frequently supports advanced protection for their formats.
Basically, there are two types of protection available:
Native protection. Not all files are born equal. Vendors have lists of formats that allow for a deeper level of protection than others. With natively protected files, you can restrict usage to read-only and assign permissions for editing, copying, and printing. For example, Azure Rights Management supports native protection for Office files, PDFs, TXTs, common image formats like JPG, JPEG, PNG, BMP, and some others (here's the full list.)
Generic protection. This type of protection works for unsupported formats. Unauthorized agents can’t open a file. But if an authorized person opens the file, you can’t control such things as copying and printing. Accordingly, authorized agents can then send information outside your zone of security comfort, and a service will only be able to remind users of the protection recommendations.
There are also other powerful players in this market like Vera Security. While focusing on Office files, Vera Security also provides an additional level of protection for file sharing in DropBox and can lock email attachments. It is currently planning to roll out email encryption.
Having a long record for both device and application usage, you can leverage interaction history to build machine learning models able to detect outlying use events. Basically, by adopting this type of threat analytics, you’ll drastically minimize any data leaks. We have discussed machine learning adoption in our 7-step strategy guide. Have a look there to understand what you can do now to embark on this initiative. Machine learning algorithms can be applied to a wide array of possibly menacing actions:
The enterprise mobility market is expected to grow to over $4.5 billion by 2020 exhibiting a 27 percent annual growth. The software is already accessible for businesses as it has an established pool of vendors, and in many aspects, is a fungible commodity. In fact, consumers usually base their choice of EMM solution on pricing, customer support, or UX/UI qualities rather than feature-set. None of the main EMM layers – 1) single sign-on and identity management, 2) mobile application management (MAM), and 3) mobile device management (MDM) – require much engineering effort to integrate.
So, the general recommendation is to start small and consider mobility management software before you hand devices to employees or upload apps to their smartphones. Then you can gradually scale to additional levels of protection like file security and advanced threat analytics.
So, BYOD (bring your own device) is no longer a trend. It’s reality. The boundary between workstation and mobile is so fuzzy, the question isn’t if we embrace enterprise mobility, but rather how we do it.
Enterprise mobility is highly efficient, unless it’s extremely harmful
Having instant mobile access to operational levers is great for the employee and the organization in general–and in theory. If you run many distributed locations where employees need to operate unified management software, opting for mobile can be very rewarding.For instance, The Walsh Group, a construction firm, embraced the BYOD demand to let their project managers share critical project information straight from the construction sites instead of going back to an office and configuring blueprints from there. This increased their cost estimation speed by 20 percent and put the company ahead of competition. For one of our clients, AltexSoft developed a customizable app for production workers to complete digital checklists when on-site, track machinery performance, take photos of malfunctioning hardware, etc. This allowed for rapid reaction and on-time employee tracking.
On the other hand, if you handle those devices or let employees use their own, you should acknowledge that humans are the weakest link in any data security structure. People lose smartphones, they install harmful software, copy information and irresponsibly paste it, or just let others access it.
That’s the problem worth considering.
How do you control access to sensitive corporate data? How do you ensure that employees won’t irresponsibly share this data? And, more importantly, how do you manage the use of mobile devices without invading employee privacy?
- Balance user accessibility. The easiest way to have your enterprise mobility strategy fail is to overregulate access to corporate resources. If your employees have to take multiple, convoluted steps just to log in, it’s likely that they will use an app only in the case of urgency. Or, they will most likely download some third-party app with the same features and better accessibility. Why should they use a laggy, overprotected corporate messenger if there’s Slack? So, consider ease of use, look and feel of software, and its performance, all of which will foster adoption.
- Choose wisely between BYOD and corporate devices. BYOD is great in terms of reducing investments in corporate hardware. On the other hand, the diversity of smartphones, tablets, laptops, and their operating systems that update differently challenges an IT department’s ability to keep current with software adjustments across myriad end-points.
- Tailor data protection measures to operational needs. Access to data differs and corresponds with how your employees engage the application. If mobility aims at tracking activities or inputting data to be further processed (as in the restaurants), access to records can be either completely or partially closed. If some data access is required, consider multilevel protection. For example, setting multiple user roles will allow you to segregate valuable data based on user type at every level.
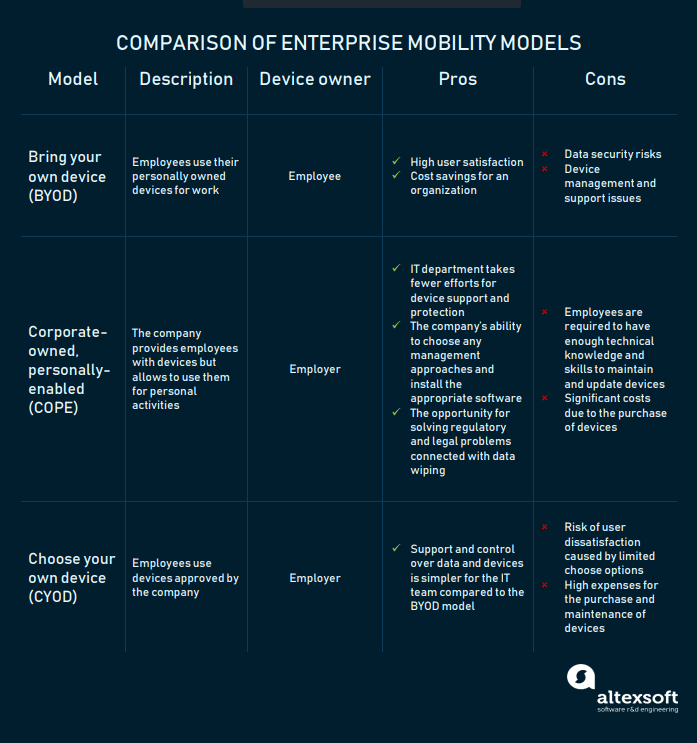
Enterprise mobility models
Organizations have developed plenty of options while searching for the optimal mobility strategy model. The three most common approaches are BYOD, COPE, and CYOD.
Bring your own device (BYOD)
BYOD, the practice of using personally owned devices at a workplace, may entail several scenarios. In the first scenario, while workers can make personal calls or send messages when at a worksite, the boss can contact them during non-working hours.The second scenario entails employees accessing corporate data when using devices for professional purposes and a company paying their cell phone bills.
Another scenario depicts employees using their devices for work and leisure, with a company choosing cell phone service options and paying for them.
Advantages: The BYOD model is convenient for users and beneficial for employers who don’t have the expense of purchasing devices.
Disadvantages: This model comes with security and management concerns due to the uncontrolled use of various devices. For example, an IT department can’t develop a unified support system due to a variety of device types and models used in an office. Employers must also consider how they will retrieve data from a worker’s device if he or she leaves the company. When the former team member worked in the sales department, special attention to data retrieval is required.
Ideally, employees must take responsibility for the integrity of business information when using a personal smartphone or tablet to reply to corporate emails, fill out checklists, or open and edit documents. The reality is that a company has to establish device use policies, explain them to employees, and implement technical solutions to help them keep both devices and data safe. So, the second and third BYOD scenarios require company solutions to technical and legal issues.
Corporate-owned, personally-enabled (COPE)
Some businesses, especially finance and healthcare organizations, find the BYOD model too risky in terms of monitoring and security and favor COPE over BYOD. These companies buy devices for workers but give them the opportunity to use them for personal tasks. Although employees don’t own the devices, they are generally in charge of their maintenance and update. That’s why this enterprise mobility model requires workers to have good technical skills.Advantages: With the COPE approach, IT departments don’t struggle with device control and protection as they know exactly how many and which devices workers have on hand. Another advantage of COPE is that organizations are free to install management software and/or integrate devices in mobile device management systems. And, we’ll talk more about that below.
This model allows for solving regulatory and legal issues connected with wiping off data on lost or stolen devices. As device owners, organizations can avoid a situation in which they have no right to remotely delete corporate data on personal devices (companies are restricted from doing so in some European countries.)
Disadvantages: The need to purchase devices is one of this model's disadvantages. Companies nevertheless can cut costs if buying devices in bulk. Employers also have more opportunity to negotiate for better service contracts because of the number of potential customers they can deliver. And as employees are responsible for keeping devices in a good technical state, the IT department can save time and money. They usually contact a device vendor or a company’s technical support only if a problem is complex.
Choose your own device (CYOD)
A company that follows the CYOD policy provides employees with one of the mobile devices from a list of approved gadgets. So, like in COPE, a company is the device owner.A worker is free to use a device they chose both for work and personal purposes. An organization maintains it by installing necessary apps and updating when needed. Usually, employees aren’t granted administrative privileges. That’s why workers must notify the IT staff about any significant settings they want to make.
Advantages: CYOD simplifies the work for the IT team because it monitors and supports a limited number of device types and models. CYOD is a good choice for companies working with sensitive information. A company has the full control over devices and can install any security software it chooses. So, corporate data is protected from unauthorized access even if a device was stolen.
Disadvantages: The implementation of CYOD has its challenges. Organizations have to spend a substantial amount of money for the purchase and/or maintenance of hardware. It’s also important to regularly update a list of approved devices not to miss new applications and technologies. Companies can keep current about cutting edge technologies with application delivery.
User dissatisfaction is another risk factor. Employees may not like the performance of the devices allowed in a company, leading to lower productivity.
One more thing to consider before going CYOD is that maintenance of different device types takes more effort for the IT team. A company has to be sure it can afford such an initiative.
Types of enterprise mobility solutions
The number of employees who run enterprise apps and work with sensitive data on their personal devices grows. In this regard, enterprise mobility (EM) solutions must address various data and infrastructure usage scenarios. When used together or in various combinations with each other, EM solutions provide safety for corporate data and a comfortable work environment for employees.There are six enterprise mobility components:
- Identity management
- Mobile application and device management
- Mobile hypervisors and containers
- Virtualized access to apps and data with virtual desktop infrastructure (VDI)
- File security and information rights management
- Machine learning-based protection
Now let’s discuss them in detail.
1. Identity management
Identity management solutions address the problem of employees using popular SaaS applications. Instead of requiring workers to use different names and passwords to access multiple applications, identity management enables employees to have a single name and password to use multiple apps.Major functionality to consider:
- Single sign-in for all applications
- Support for apps used by your organization
- Group access management, which allows managers to assign access to employee groups without enumerating any users in particular (those who can log into apps). This also implies setting specific access rules, like all users from sales departments in the US and Canada can access this app.
- Multi-factor authentication that supports additional levels of verification besides single sign-in
- Some services provide advanced reports that employ machine learning techniques to identify anomalous sign-ins (unknown sources, irregular sign-ins, suspicious IPs, etc.), usage reports, error reports, activity logs, and others.
- Remote access to on-premise software
Obviously, each vendor integration scenario may differ, but generally, the following steps are advised:
- Research the authentication requirements that your enterprise mobility vendor has.
- Check whether your app authentication matches them. If it does, most likely app integration will take only administrator-level effort.
- If they don’t match, you’ll need additional app customization to meet these requirements.
- Consider integration at the developmental stage. If you just plan to build a custom app and consider Microsoft Identity Management, you can approach the development with further integration in mind. Microsoft elaborately lists authentication scenarios for developers to make apps compatible with Microsoft AD.
- Enable support of SAML 2.0 or have an HTML-based sign-on page. You can update an existing app following the requirements. Once you have it enabled, an administrator can use a dedicated tool for integration.
- For Xamarin apps, use Xamarin.Auth. We’ve already discussed Xamarin pros and cons in detail. To sum up the conclusions, Xamarin technology is great for enterprise apps if you opt for cross-platform development and BYOD. For Xamarin-based apps, there’s a convenient way to integrate them in two simple steps.
2. Mobile application and device management
MAM/MDM solutions are built around the idea of both device and application management for corporate users. Basically, they provide dashboards and management environments to track and remotely control devices and apps across all major platforms (Android, iOS, and Windows). Usually, the functionality of these products can be divided into two general task groups: device management and application management.Application management. The MAM features are designed to meet the BYOD scenarios, when your employees actively use their own devices for work but aren’t thrilled about letting an organization intrude on their private lives. Employee use of a single device where private and work-related usage mix may raise a number of security concerns. MAM allows for decoupling personal and job use by managing applications without sacrificing users’ privacy. This means that you can impose rules and regulation for work-related apps allowing free use of the others.
Some things to consider:
- Block copy and paste
- Block “save as” and backup to a personal cloud
- Impose PIN-access to apps
- Update apps remotely
- Erase sensitive data from device memory
- Require all work-related links to be opened within a dedicated, managed browser, etc.
- Define available apps that users can install or those that are automatically installed as a result of enrollment
- Define compliance rules that evaluate which devices can be enrolled
- Manage security settings on devices
- Set conditions under which apps and resources (e.g. corporate emails) can be accessed
- Assign certificates and VPN/Wi-Fi profiles to users of an enterprise infrastructure
- Remotely erase data from managed devices, etc.
Most EMM systems–like industry leader AirWatch–have geofencing support. This allows for defining geographic zones connected with specific policies. For example, many hospitals provide their staff with tablets having clinic management software to record patients’ symptoms and instantly retrieve patient-related information. To ensure that sensitive patient data is safe, geofencing can lock this tablet if it were to leave the hospital’s defined perimeter. Basically, you can tether any policy to a device’s geographic zone.
How to integrate apps with application management solutions. Like identity management, popular EMM vendors support integration with certain apps available at the AppStore or in Google Store. If your app isn’t on the list of supported ones, you’ll need programming to enable this integration. Usually, there are two paths you can take:
- Use app wrapping tools. Integration may be relatively straightforward if you have a simple app. Wrapping allows you to manage applications without directly tweaking their source code. In fact, wrapping is a technique that implies that the app code will be automatically decompiled and specific functionality will be replaced for application management. Obviously, this method has a lot of limitations and is recommended for tactical use. Generally, wrapping will allow for relatively basic management like data transfer limitations, blocking copy and paste, blocking screen capture, etc. To provide a profound MAM, you’ll need SDKs.
- Use vendor-provided software development kits (SDKs). An SDK is a set of libraries and tools for software engineers to implement the functionality compatible with a given software. In terms of MAM, using SDK entails tweaking the source code of an app or developing it with further application management in mind. For instance, using AirWatch SDK you’ll be able to manage password policies, data encryption, integration authentication, etc.
3. Mobile hypervisors and containers
Mobile virtualization is an efficient technique for supporting the BYOD policy within an organization. It allows an employer to keep corporate data secure by implementing device use policies while giving an employee the ability to use personal devices for work. What’s more, this approach ensures the privacy of both employer and employee.Virtualization can be done through hypervisors and containers.
Hypervisor (also known as virtual machine monitor/manager) is a software used to create and run multiple operating systems (OSs) on a device (host machine). The additional OS is called a virtual (guest) machine (VS).
Containers allow for abstracting applications from one computing environment to another. They provide a virtual isolated platform for applications to run on.
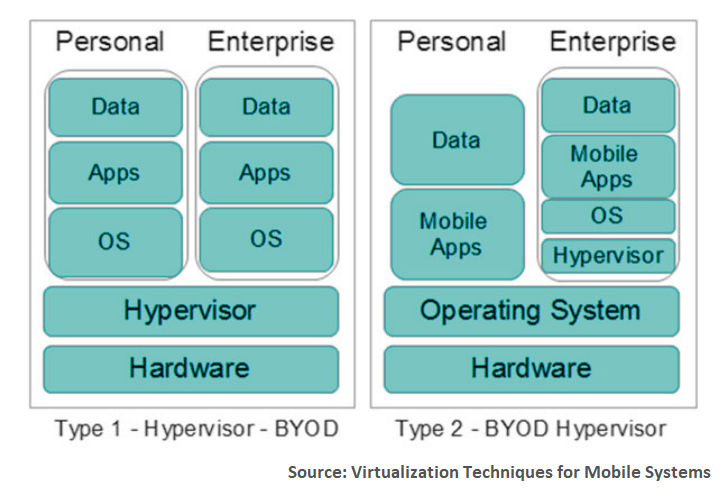
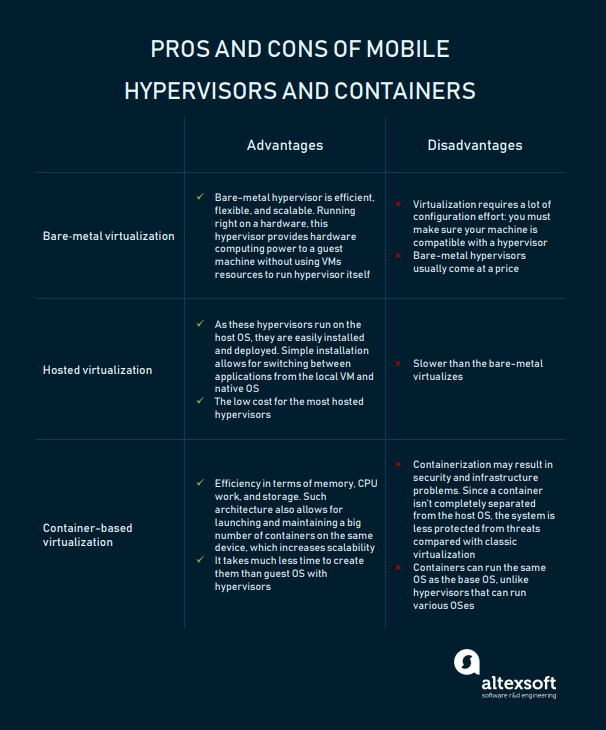
Virtualization with hypervisors
This solution entails using mobile hypervisors to separate personal and business content on a single device. A hypervisor allows for running personal apps on one OS and business apps on the other, more secure OS. So, the user can access company data only with enterprise apps. At the same time, an organization has no means to intrude on a worker’s privacy.There are two types of virtualization via hypervisors.
Bare-metal virtualization. This type of hypervisor runs directly on the device hardware and has access to its resources. This allows for optimizing performance of both OSs. As these OSs are completely separate from each other, possible crashes, errors, or malware attacks on the former OS won’t affect the latter.
Because of such placement, bare-metal hypervisors are developed specifically for hardware visualization. In other words, they manage and control the work of numerous applications within various VMs. That’s the reason IT departments prefer to use them in production.
Hosted virtualization. This hypervisor runs within a host mobile system software environment, between the hosted OS working on the second software level and a guest OS that runs on the third software level. The hypervisor is installed on top of the guest OS, like any other app. This virtualization approach is less secure because the performance of the guest OS depends on the host OS. So, the guest operating system may fail if the host is attacked.

How to implement virtualization via hypervisors. The biggest virtualization vendors — VMware, Microsoft and Citrix Systems — provide hypervisors of both types. If bare-metal hypervisors work best for you, then consider such hypervisors as Oracle VM server, Microsoft Hyper-V, and ESX or ESXi by VMware. When looking for a hosted hypervisor, think about installing Microsoft Virtual PC, Oracle VirtualBox, Workstation, Server, or Fusion by VMware.
Virtualization with containers (application containerization)
This approach, sometimes referred to as OS-level virtualization, entails separating mobile devices via containers. Unlike hypervisor-based virtualization, containerization doesn’t require launching an extra OS (virtual machine) for each app. Containers are running on a single host OS and access a single kernel, so are more efficient than VMs. Briefly said, containers visualize OS instead of hardware.Containers store files, system libraries, and environment variables — the components needed to run a specific software. The host OS also restrains the container's access to physical resources like CPU and memory. Thanks to this, the container uses less of the host OS physical resources.
The mobile device has personal and enterprise environments. The work environment is supported by the IT administrators, while a user is free to do anything within the personal environment. The container can be deleted if a device is stolen, lost, upgraded, or if an employee leaves the company.
How to implement container-based virtualization. Many tools for containerization are available on the Internet, both open source and paid. Here are some of the free options you can choose from.
Docker is one of the most popular providers of containerization tools. Its open source platform allows for creating and operating containers for Linux- and Windows-based apps. Docker containers are portable: You can move them among any system that shares the host OS without changing code.
Kubernetes, another free container orchestration engine, also has a big user community. The tool can help you control and maintain the work of numerous containers, so it’s especially valuable if you have to manage large-scale operations. The Kubernetes platform can be integrated with the Docker platform.
OpenShift is a powerful container management platform that “brings Docker and Kubernetes to the enterprise.” Integration with the latter engine allows users to automate development, deployment, maintenance, and scaling of containers.
Containers and hypervisors compared
VM-based systems include a complete OS along with drivers, binaries or libraries, and then the application itself. As a container shares the host OS and holds a single application with related binaries or libraries, it doesn’t consume as much server hardware memory as VMs. Containerization is, therefore, a more efficient approach in terms of memory, CPU work, and storage. Such architecture also allows for launching and maintaining a large number of containers on the same device, increasing scalability.
4. Virtualized access to apps and data with virtual desktop infrastructure (VDI)
Virtualized access to apps and data when applied to mobile use cases gives employees the opportunity to access enterprise apps remotely while reducing a company’s infrastructure maintenance expense.While virtualization via hypervisors or containers and virtual desktop infrastructure (VDI) allows organizations to solve similar management and security problems, they significantly differ in the data storage approach.
VDI (sometimes called server-based computing) entails running and managing a desktop OS in a data center instead of a local computer, thin client, or mobile device. The desktop image is delivered on-demand via a remote display protocol, while corporate information is securely stored in a data center. It has no difference for the user.
At the hardware level, VDI consists of a group of host machines providing computing power to connected devices.
Organizations may choose between persistent and nonpersistent approaches to VDI. The former is about providing a worker with a personal desktop image that can be configured according to their needs. The latter entails visualized desktops for public use within the organization. These desktops return to their original state after a user logs out.
Advantages: Besides ensuring safety for data, VDI allows for cost savings related to infrastructure upgrade. Thanks to a little computing taking place at endpoint devices, IT can turn obsolete desktops into VDI clients extending their lifespan. And when it’s time to buy new machines, a department can get less powerful ones.
However, the storage of OS, data, apps, and settings for users required for persistent VDI at a data center may come at a high price. So, a company must determine it has enough resources to use this visualization technology.
Disadvantages: VDI also has some drawbacks. The network connection may fail at times, and if it does, the whole team’s productivity is in danger. The licensing and support for software is another VDI’s weak spot. Companies using noncustomized desktop images have even more chance of facing problems with licensing. The reason is that some agreements prohibit providing software for numerous devices.
How to implement virtual desktop infrastructure. The first thing you should do is to compare VDI platforms in the market. We suggest looking at XenApp and XenDesktop by Citrix (the vendor provides a 90 day trial period), Horizon 7 by VMware, and solutions from Microsoft.
5. File security and information rights management
The file-security concept focuses on data files instead of devices and apps. How does that work? Basically, as with previously discussed types of software, you can impose specific policies on files and define who is allowed to see stored information. Usually, these services provide three types of policies: encryption, identity, and authorization. You can also configure such things as rights to read, edit, and print documents. Another good feature is usage monitoring. Even if a file leaves the boundaries of your organization (e.g. is sent to subcontractors), you’ll be able to track when and whether specified people opened the document, as well as whether unspecified people attempted to open this document. Or… succeeded in opening it.Yet, as always, there are some limitations. For instance, if you are a Microsoft fan and its products are ubiquitous in your organization, it’s likely that you store information in Office files. Well, it’s better to use Azure Rights Management if you do, because Microsoft frequently supports advanced protection for their formats.
Basically, there are two types of protection available:
Native protection. Not all files are born equal. Vendors have lists of formats that allow for a deeper level of protection than others. With natively protected files, you can restrict usage to read-only and assign permissions for editing, copying, and printing. For example, Azure Rights Management supports native protection for Office files, PDFs, TXTs, common image formats like JPG, JPEG, PNG, BMP, and some others (here's the full list.)
Generic protection. This type of protection works for unsupported formats. Unauthorized agents can’t open a file. But if an authorized person opens the file, you can’t control such things as copying and printing. Accordingly, authorized agents can then send information outside your zone of security comfort, and a service will only be able to remind users of the protection recommendations.
There are also other powerful players in this market like Vera Security. While focusing on Office files, Vera Security also provides an additional level of protection for file sharing in DropBox and can lock email attachments. It is currently planning to roll out email encryption.
6. Machine learning-based protection
Another effective way to enable mobility security is to employ machine learning techniques to detect abnormal and potentially hostile activities. Some software packages have machine learning-based solutions out of the box, which can greatly simplify the implementation of this layer of protection. For example, Advanced Threat Analytics is included in Microsoft’s EMM Suite. If your vendor software doesn’t support such advanced analytics, consider engaging a consultant to assess your EMM infrastructure.Having a long record for both device and application usage, you can leverage interaction history to build machine learning models able to detect outlying use events. Basically, by adopting this type of threat analytics, you’ll drastically minimize any data leaks. We have discussed machine learning adoption in our 7-step strategy guide. Have a look there to understand what you can do now to embark on this initiative. Machine learning algorithms can be applied to a wide array of possibly menacing actions:
- reconnaissance activities
- finding compromised credentials (e.g. account credentials are sent in plain text or some account shows abnormal working hours)
- lateral movements (finds abnormal resource access), etc.
Consider Enterprise Mobility and Security Early
Employee mobility and BYOD are disruptive trends in terms of enterprise security. As corporate information becomes increasingly accessible, we should address this threat early in a smart and balanced way.The enterprise mobility market is expected to grow to over $4.5 billion by 2020 exhibiting a 27 percent annual growth. The software is already accessible for businesses as it has an established pool of vendors, and in many aspects, is a fungible commodity. In fact, consumers usually base their choice of EMM solution on pricing, customer support, or UX/UI qualities rather than feature-set. None of the main EMM layers – 1) single sign-on and identity management, 2) mobile application management (MAM), and 3) mobile device management (MDM) – require much engineering effort to integrate.
So, the general recommendation is to start small and consider mobility management software before you hand devices to employees or upload apps to their smartphones. Then you can gradually scale to additional levels of protection like file security and advanced threat analytics.
